Twitter was recently hit with a security problem when the website was hacked, leaving a quarter of a million accounts in limbo. Weeks earlier, Zappos suffered the same issue. These are examples of how even the strongest passwords can be at risk. However, being the Internet users we are, we aren’t just going to pack up our digital lives and forgo the Internet altogether.
We must improve our current password practices and ensure that the day-to-day scammers and hackers don’t find the key to our online lives. Today, I present you with the comprehensive guide to everything about passwords. From how to choose a strong password to what to do afterwards.
Password Boot Camp
What better way to start a guide to passwords than by helping you create the ultimate password? To start, have your computer near by along with a writing utensil and a notepad- they’ll come in handy during this process, and are all that you’ll need. No need for dictionaries or a second individual—your password doesn’t have to be, and shouldn’t be, complicated and highly complex. Below are a couple of tips on how to get started:
1. Make Personal Passwords Non-Personal – One key tip is to ensure that your password is related in some way to you that will be easy for you to remember, while not including easily identifiable information. What does that all mean? Yes, you can work in your favorite color or television show into your password. However, don’t include your address or birthday in there.
2. No Random Generators – Password generators are always considered recommended for choosing strong passwords, but I always advise staying away from them for two reasons. First, some generators heavily reuse password suggestions. Secondly, they are much harder to remember and will require to resorting to password recovery frequently.
3. Break the Molds – I advise not making use of real words or phrases in your password. For example, if you are going to include the word “soccer” in your password, use “$0kr” instead. This also means, don’t make use of dictionaries in consulting your next password—that’s just asking for hackers to come to you like fresh bait.
4. The NAC Philosophy – The philisophy I just created while making this article is the NAC philisophy. This means ensuring that your password includes “Numbers A Characters” along with text. One common mistake with passwords is only including letters, but also including characters and numbers strengthens your password. Simply changing “LuvToPlaySoccer” into “!Luv2ply$okr!” turns a weak password into a strong one.
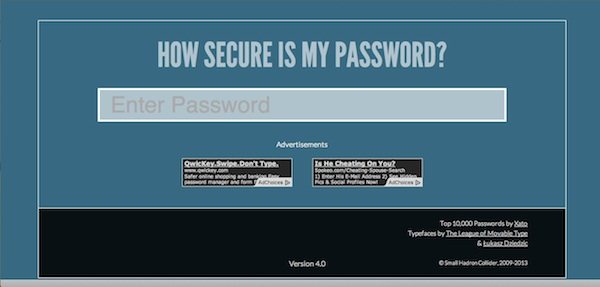
5. Utilize the Strength Test – Finally, making use of a strength test can ensure that your password is top performing. Several online resources, including How Secure Is My Password, allows you to instantly see how strong (or common) your password truly is.
Divide and Conquer
It’s important to have a different password for each service that you use. It seems a bit difficult in the beginning, but when you begin to continually use the separate passwords for the separate services, you will find yourself associating one password with the service that matches it.
When you use a separate password for each website, make sure that you don’t simply leave out a letter or include an extra number—that’s not considered a true variation, and truthfully, it helps narrow down the hacker’s choices even more. So how do yourself to remember all of these passwords? Making use of applications for your desktop or mobile device is a huge help.
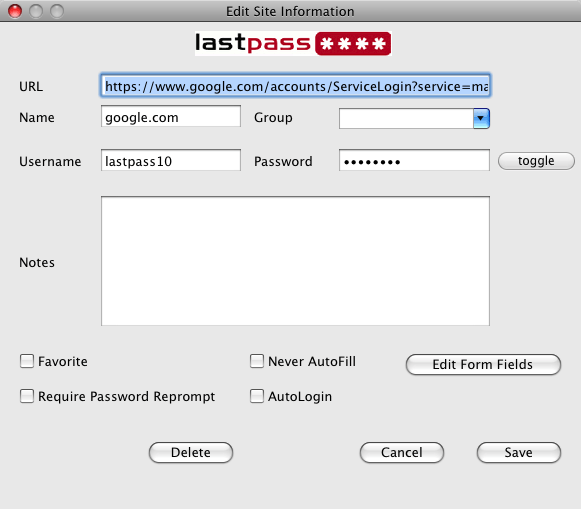
I highly recommend Passwords Plus or KeePassX. Both services are cross platform, have high encryption protection, as well as support for saving the passwords and codes of various services that you use. LastPass is another well rounded password manager that I recommend for users to make use of.
Secrets In the Details
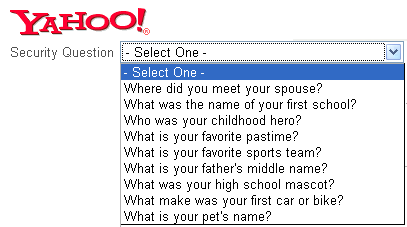
You have a great password, wonderful. Now what happens when you forget your password? No problem, just go to password recovery and answer a few questions and you’re done, correct? Well this “convenience” is more of a convenience for hackers than yourself. Many times, when asked to create a recovery answer to a question, we always pick the easiest ones to answer to quickly get through the process.
However, if your hacker already has the password to your email and is looking to extend its reach, they will make use of your easy-to-answer recovery questions to increase their control over your personal life. How do you protect yourself from hackers passing the recovery test?
Answer questions truthfully but in a way that isn’t technically the norm. In other words, look to your recovery answers as passwords of their own. For example, if your question is “In which city were you born?” and your answer is Los Angeles, consider going a step further and including the state as well (even when asking for just a city), or spell the city in a different way, like *Lo$$ Angele$* instead of Los Angeles.
A friend I consulted while creating this article mentioned a final tip: create an email address specifically for recovery. It may seem like a hotbed of all of your passwords, in one place, but if you ensure that you use the recovery only when you need it and emptying out your trash each time you make use of the password, an individual who hacks that email will be presented with an empty inbox—forcing them to target their prey elsewhere.
Special iOS Consideration
Finally, what’s the deal with iOS passwords? It seems that your FBI, secret spy, creative password production ends at this point. Most iPhone, and mobile users in general, seem to resort to simple passwords for their phones. This is worse than doing so for your social network, for example, because there is a greater likelihood of someone going into your phone than hackers in your website or services.
This could be because our idea of hackers is a bit distorted: from the teenager in a dark room trying to crack password codes, to your nosy friend who’s trying to go into your phone to take a peak at your text messages, both individuals are considered hackers. Chances are you’ll encounter the friend situation much more often. Below are a couple of quick tips on creating the ideal mobile password for iPhone users and how to increase your security even further:
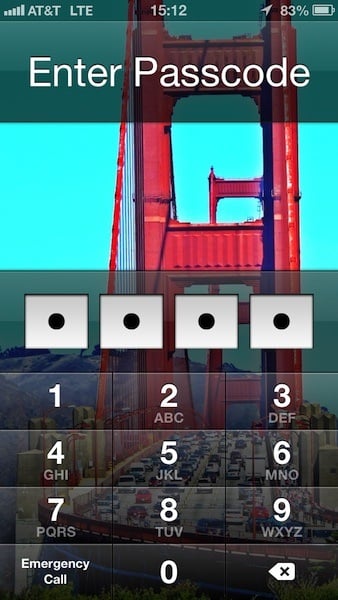
- Avoid Patterns: With only 10 numbers to your disposal for only four spots, it’s important to not have corresponding numbers used in your code. This means that 1234 is out, 0987, is out, and the like.
- Match Numbers with Letters: You may not have noticed, but the keypad on your iPhone also has letters associated with the numbers, also known as T9. This makes it easier to associate a mini phrase to numbers. For example, RAYS = 7297 or WANT = 9268.
- Look into Longer Passwords: iOS also allows you to make use of text passwords as well. Going into Settings > General > Passcode Lock > turning off “Simple Passcode” makes this happen. Make sure you abide by the tips mentioned in this article when going by this route.
- Limit Access from Lock Screen: In the same settings area, you can also change what you allow access to when locked. You can prevent Siri, Passbook, and Reply with Message to be accessible from the lock screen. You can also erase iPhone data after 10 failed passcode attempts from here as well. However, I recommend against using that unless I’m traveling or in a compromising venue (a concert, for example).